iPSK IMPLEMENTION
With the advent of internet of things, the number of devices
that connect to the internet is increased multifold. Not all of these devices
support 802.1x supplicant and need an alternate mechanism to connect to the
internet. One of the security mechanisms, WPA-PSK could be considered as an
alternative. With the current configuration, the pre-shared-key is the same for
all clients that connect to the same WLAN. In certain deployments such as
Educational Institutions, this results in the key being shared to unauthorized
users resulting in security breach. Therefore, above mentioned and other
requirements lead to the need for provisioning unique pre-shared keys for
different clients on a large scale.
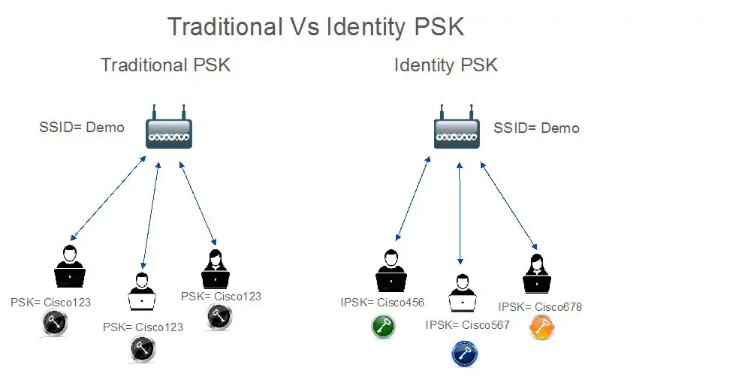
- Identity PSKs are unique pre-shared keys created for
individuals or groups of users on the same SSID.
- No complex configuration required for clients. The same
simplicity of PSK, making it ideal for IoT, BYOD, and guest deployments.
- Supported on most devices, where 802.1X may not, enabling
stronger security for IoT.
- Easily revoke access, for a single device or individual,
without affecting everyone else.
- Thousands of keys can easily be managed and distributed
via the AAA server.
DEVICES-WLAN
is created for connection for DEVICES which are not supporting 802.1X
authentication and no NORMAL PSK authentication.
DEVICES-WLAN created for these DEVICES access the Wireless Infrastructure, This WLAN is using iPSK(IDENTITY PSK) process to connect the devices in this WLAN.
Please find
the below LINK for getting Benefit over Tradition PSK to iPSK = Identity PSK
Reference:-
2.
REQUESTED
CONFIGURATION ON WLAN
MAC FILTER + PSK should be configured, PSK is Dummy Value.
RADIUS SERVER which is providing the Identity
Authentication for DEVICES
The SERVER having TWO ROLES:
1.
RADIUS and
RADIUS PROXY ROLE
2.
ACTIVE
DIRECTORY (Separate from ANGLO DOMAIN) in different Forest
Oct 24 21:17:59.117:
[SA] a4:c3:f0:b1:b0:89 Values before applying NASID - interfacetype:0, ovrd:0,
mscb nasid:MOBILITY-WLAN, interface nasid:, APgrpset:0
Oct 24 21:17:59.117:
[SA] a4:c3:f0:b1:b0:89 Set Clinet Non AP specific WLAN apfMsAccessVlan = 402
Oct 24 21:17:59.117: [SA]
a4:c3:f0:b1:b0:89 This apfMsAccessVlan
may be changed later from AAA after L2 Auth
Oct 24 21:17:59.117:
[SA] a4:c3:f0:b1:b0:89 Cleared localSwitchingVlan, may be assigned later based
on AAA override
3.
DEVICES-WLAN DEVICES
AUTHENTICATION PROCESS
THE DEVICE. Local Server has two roles : RADIUS and AD(for DEVICES)
·
The SSID
using the Identity PSK authentication where all Machine/Devices MACs must be
created as users in Active Directory (with the MAC address as the user and
password)
·
USER
Identity MAC configure as username and password on AD and then it is a part of
one AD Group (like SCANNER) , on Radius part we have called this group in
location policy (VLAN tag and PSK : https://passwordsgenerator.net/ )
·
WLC
should configure with SSID where MAC filter and PSK (Common any) use as
pre-requisite Role of WLC is when user connecting on SSID it passed that
request to NPS Server where we have configured Identity USERNAME “MAC” and
PASSWORD “MAC” as well as we configured the RADIUS PSK and VLAN information for
that DEVICE GROUP which send that information to WLC and WLC will compare the
configured PSK on DEVICE-WLAN in DEVICE and received PSK from Radius and
then authenticate user to process for DHCP.
RADIUS SETTING





No comments:
Post a Comment